Cyber Security researchers are today discussing the pros and cons of paying for a dump of exploits currently held by a notorious hacking group called The Shadow Broker’s. If these exploits get into the wrong hands they could be used to steal credit card information, login credentials or take control of a computer remotely.
This debate on how to deal with #ShadowBrokers that @hackerfantastic and @x0rz have spawned is interesting to observe.
— Nex ~ Claudio (@botherder) May 31, 2017
It is unclear how the Shadow Broker’s acquired the exploits. It has been speculated that an NSA operator left it on an insecure remote server. An exploit is a piece of code used to abuse a flaw in a system or software. The hacker can then install malicious code known as malware onto the vulnerable system.
The issue produced a lot of debate on Twitter with people offering arguments for and against paying for the exploits.
AGAINST
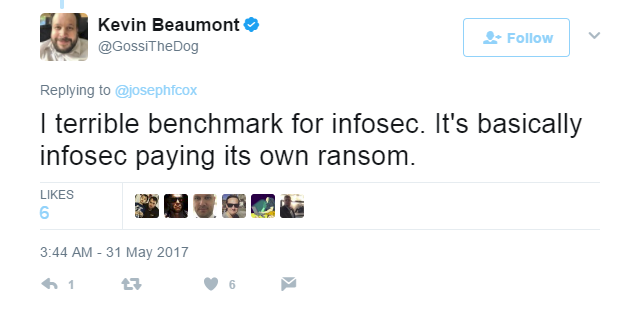
Kevin Beaumont, a UK based security researcher said that the prospect was a new low for infosec.
If InfoSec vendors fund Shadow Brokers ($20k per monthly subscription) leaking Nation State tools I think it's a new low for InfoSec.
— Kevin Beaumont (@GossiTheDog) May 30, 2017
Beaumont tweeted that the situation amounted to the infosec community paying a ransom for stolen goods.
Alan Woodward, a Security Advisor, stated that paying The Shadow Broker’s “would encourage further such thefts, and so I’m afraid as much as I’d like to see what they have to say, I think it’s a poor idea.”
Some have said that paying for The Shadow Broker’s dump would be supporting terrorism.
FOR
Others have argued that the purchase would offer a chance to patch, or fix, the problems before the exploits could be used for criminal purposes.
Mathew J Schwartz tells us that “[the] Goal of crowdfunding by security researchers is to prevent future wannacrys.” This is something that would be welcomed by all the people who were inconvenienced by WannaCry. The WannaCry worm infected machines across the globe and crippled organizations such as the NHS (National Health Service), in the UK.
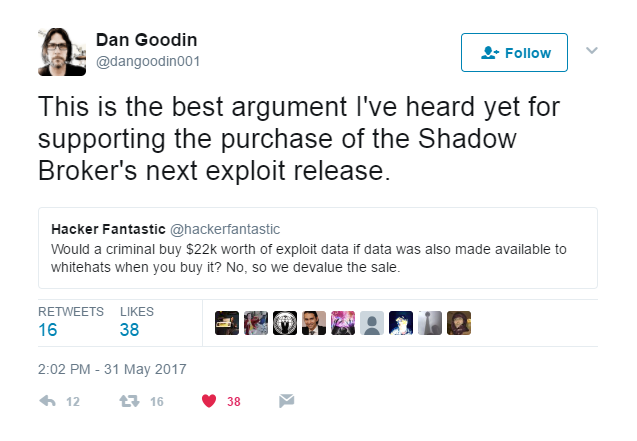
Dan Goodlin tweeted that the the best argument is that the purchase of exploits by whitehats devalues the exploits, therein rendering it little to useless to other, possibly more malevolent buyers.
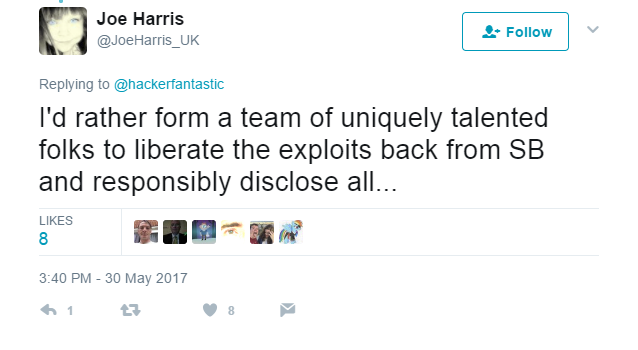
Joe Harris, Creator of the Threat² CTI Model, tweeted his preferred solution to the issue.
According to The Shadow Broker’s, to obtain access to the dumps yourself, you have to purchase 100 ZCash (close to $20,000) and send the money to the The Shadow Broker’s z_address, making sure you include your email address. If you correctly follow these steps, on July 1st, you will have received an email with a link and a password to the dump of that month.
Wow, Shadow Brokers is launching a monthly subscription service for new NSA data dumps. ? https://t.co/kIRCJSoC0q pic.twitter.com/TqtCMGZDcC
— Mustafa Al-Bassam (@musalbas) May 16, 2017
According to a Shadow Broker’s article, the subscription service will provide subscribers who pay a fee of $20,000 per month with:
- Web browser, router, handset exploits and tools
- Select items from newer Ops Disks, including newer exploits for Windows 10
- Compromised network data from more SWIFT providers and Central banks
- Compromised network data from Russian, Chinese, Iranian and North Korean nukes and missile programs
Matthew Hickey, a hacker and Cyber Security Expert, acknowledged the debate, the divided opinions and set up a pole to find out if people thought crowd funding was a legitimate solution.
Is a KickStarter project to pay Shadow Brokers subscription ($20k) and then perform analysis on it and responsible disclosure a good idea?
— Hacker Fantastic (@hackerfantastic) May 30, 2017
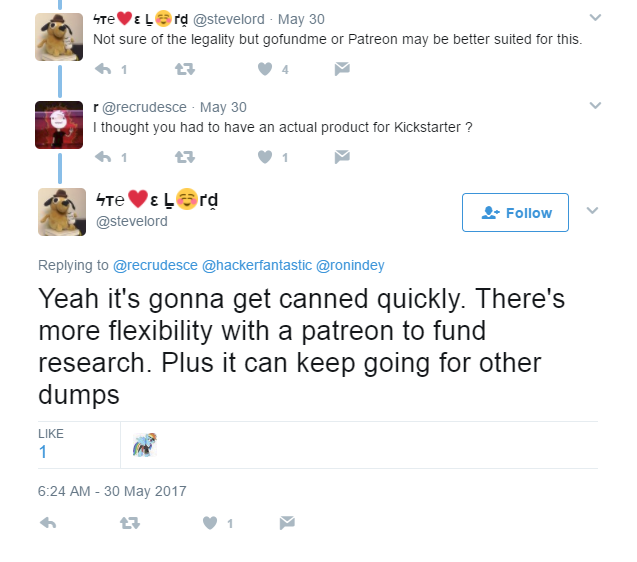
Steve Lord suggested a patreon was made.
Hickey tweeted that he had made a patreon and would go ahead with collecting funds to pay the subscription fee.
We (@x0rz and me) have decided to attempt to crowd source the funds and buy the @shadowbrokerss exploits – details https://t.co/xLkgIgomg7
— Hacker Fantastic (@hackerfantastic) May 30, 2017
Joseph Cox, who covers hackers for Motherboard, summarised the plan to crowd source the money to pay the subscription fee.
Using Patreon to buy Zcash to get NSA exploits to stop the next wave of ransomware infecting hospitals. Future, man https://t.co/V5hFkq2A39 pic.twitter.com/fuGjPGJHML
— Joseph Cox (@josephfcox) May 31, 2017
On April 14th, 2017, the The Shadow Broker’s released an exploit kit known as Fuzzbunch, similar to Metasploit, which contained zero days such as EternalBlue. A zero day is a vulnerability or exploit that is unknown to the vendor or is unpatched. Eternalblue was utilized by the WannaCry worm to infect machines across the globe and cripple organizations such as the NHS (as mentioned briefly earlier), thus forcing them to deny requests.
Hickey added to the arguments for:
Just by having this fundraising present distracts other criminals from attempting to buy the tools as they would not retain monetary worth.
— Hacker Fantastic (@hackerfantastic) May 31, 2017
Brendan Dolan-Gavitt, Assistant Professor at New York University Tandon, commented that the future as imagined in cyberpunk culture is happening right now.
Crowdfunding to buy nation state exploits from an anonymous group using untraceable cryptocurrency. The future got real cyberpunk real fast. https://t.co/DQeyaJloX8
— Brendan Dolan-Gavitt (@moyix) May 30, 2017
One unanswered question is why didn’t The Shadow Broker’s auction the FuzzBunch framework? Aren’t exploits effecting a popular operating system, i.e Windows, more useful than ones affecting a system infrequently used by the masses? After all, Windows is more often to be found on the average user’s computer. Is the motive something other than monetary gain? Maybe, maybe not. In the end, the cards will all play out and we may get to see the repercussions of these much sought after exploits.
The post Should Security Researchers Pay For The Shadow Broker’s Exploit Dump? appeared first on We Are Change.
from We Are Change https://wearechange.org/security-researchers-pay-shadow-brokers-exploit-dump/



No comments:
Post a Comment