After the Wannacry ransomware attack infected systems across Europe and the Americas in May 2017, a new malware known as Petya arose Tuesday morning and spread through the Ukraine, Russia, Poland, Italy, Belarus and a few instances in the US.
This is what users saw on their screens. Petya tells its victims their files have been encrypted which means people would no longer be able to access their files. It then demands $300 in bitcoin (BTC) to be paid to a BTC address and only then will your files be decrypted. Petya claims you have no way of recovering your files without paying the ransom.
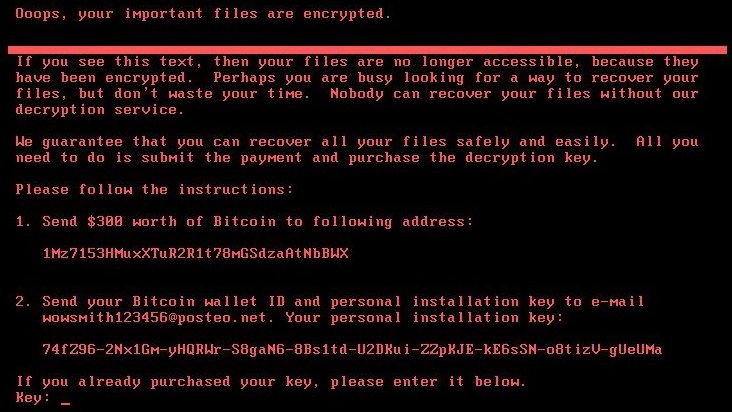
Infected computers display a message demanding a Bitcoin ransom
Petya utilizes the EternalBlue (EB) exploit in a similar way to the Wannacry worm. It also abuses Windows tools such as Windows Management Instrumentation (WMI) which is used to automate tasks and PsExec which is used to remotely manage and execute processes with the use of valid credentials i.e. username and password.
What this means is that someone could log into your computer with your login details and execute programs remotely. In a corporate setting, it is common for all the computers to accept the same login details. The worm would steal login details from one computer and use them to log into other computers on the local area network or LAN. This enabled the worm to spread quickly.
After Wannacry, many systems were patched against the EB exploit. A patch fixes what is broken in a system. This stopped Petya from spreading any further across the globe than it already did.
The worm is thought to have originated in an update from a Ukrainian accounting software program known as Medoc. A firewall would normally be present to prevent any outside attackers from entering a network. The update allowed the malicious code to be downloaded and unwittingly executed by the users through the Medoc software. This allowed the attacker to bypass the firewall and the worm to enter the network without the use of exploit code.
Docme was accused of spreading the worm via its update service but the company denied these claims. A research firm known as Talos Intelligence discovered a forged digital signature belonging to Medoc within the payload. In the same way a signature can be forged on a check, the digital signature allowed the payload to identify as one originating from Medoc. The signature would allow an attacker an open door into a system running Medoc without raising any alarm.
Companies such as DLA Piper, a global law firm, as well as MSDInvents, a global healthcare company, were affected by the attack. Two popular multi-national companies affected were a shipping giant called Maersk and a pharmaceutical company called Merck. A majority of Petya infections occurred in the Ukraine and Russia, as shown in this graph.
Current situation of Petrwrap/wowsmith123456 ransomware – percentage of infections by country. pic.twitter.com/Q42WPlBlja
— Costin Raiu (@craiu) June 27, 2017
Matt Suiche, a French hacker and founder of cyber defense firm Comae Technologies, discovered that the Petya virus was actually built to wipe the disk of the victims rather than encrypt the disk as Petya initially portrayed. The ransomware message was nothing more than an attempt to cover up its true purpose. Its real intention was to wipe the disk which would result in the loss of all files without the ability to recover them.
Suiche’s blog states:
“After comparing both implementation, we noticed that the current implemented that massively infected multiple entities [in] Ukraine was in face a wiper which just trashed the 25 first sector blocks of the disk.”
According to Hacker Fantastic, if the user sees this message he or she should power off the computer immediately. Following these instructions would allow you to safely recover your files and prevent the loss of data.
If machine reboots and you see this message, power off immediately! This is the encryption process. If you do not power on, files are fine. pic.twitter.com/IqwzWdlrX6
— Hacker Fantastic (@hackerfantastic) June 27, 2017
The update server for Medoc was not secure from attackers. The attackers may have been a nation-state since normal ransomware is designed to extract bitcoin or other payment from victims. There would be no point paying a ransom for a wiped drive.
“Petya.2017 is a wiper not a ransomware” by @msuiche – Was a nation state attack in disguise. ? #PetrWrap #Petya https://t.co/VlTB0cqRPV
— Mark (@sneakymonk3y) June 28, 2017
The post Destructive Petya “Wiper Malware” Attack Spreads Fast appeared first on We Are Change.
from We Are Change https://wearechange.org/destructive-petya-wiper-malware-attack-spreads-fast/



No comments:
Post a Comment